
How Does Netskope Benefit the Public Sector?
Author: Oliver Knapp
Release Date: 18/10/2024
The public sector presents a unique security use case where the sheer amount of data proves to be an enticing, treasure trove for attackers to get their hands on, be that for the purposes of crippling infrastructure, or committing financially motivated crimes such as identity theft. To that end having software which can control, react and provide insight to the data and the accesses being made to it is of utmost importance.
This is where the comprehensive and multi-faceted approach presented by Netskope comes in and provides an incredibly robust platform from which security administrators can defend the data and records of millions of persons. Be that through Netskope’s ZTNA (zero trust network access) capabilities and DLP policies, or through its granular app control and threat protection facilities. In this blog we will explore this and more from the perspective of leveraging the entire Netskope platform to benefit the public sector.
What Are the Threats to the Public Sector?
As previously stated, the public sector is in a unique position where the amount of sensitive data flowing through it and being stored is of a magnitude that is not found replicated in many other companies and areas. This makes it a promising target for a manor of different attackers, be that those driven by monetary gain, or by political motives due to the fact that it is intrinsically linked to government. Attacks on the NHS can be seen as happening as recently as 2 months ago (as of writing) with the Synnovis attack, and has played host to arguably some of the most prolific cyber attacks ever, such as the WannaCry attack in 2017.
Malicious Attackers
A broad term for those motivated by individual goals such as monetary gain or identity theft. Malicious attackers gaining access to public sector devices such as personal or work computers and stealing credentials to gain access to accounts and, as such, the ability to move laterally through the network presents a unique challenge to deal with. From this lateral movement, if access rights are not put in place, attacks such as worms, ransomware and backdoors can be deployed into the systems. Without an internal tool which can look at, alert on and control unauthorised access and use, this method for attack can become a reality. These attacks usually originate from a phishing attack as per Gov.uk showing that 84 percent of cyber attacks were due to phishing and as such having effective education and phishing prevention is key, netskope can facilitate this.
Insider Threats
When we talk about insider threats we are talking about those within the organisation, who, for whatever reason, want to perpetrate cyber attacks. Usually this is in the form of data exfiltration for an outside entity or installing back doors and facilitating cyber attacks the same way an adversary would. To the end of protection and prevention then, a tool which can provide control over internal resources and data is paramount and proxying resources becomes a valuable method of defence.
A key theme that can be found when looking at the methods employed by insiders is that they aim to remove or copy data outside of the organisation, and to that end. Having competent DLP becomes incredibly important. As managing what data can leave managed apps at all times, can go to massively mitigate the damage an insider can do.
Corporate and International Threats
Often a threat base which is not massively considered when looking at cyber attacks is that of politically motivated groups, other governments and corporate entities. These individuals or groups will often gain access in ways not dissimilar to the previously talked about malicious attackers, although their motives will most of the time not be financial or identity theft. They will be aiming to cause disruptions or steal large amounts of data relevant to the company. In the public sector this would potentially be the details of higher ups or confidential projects. To that end, advanced and sophisticated DLP techniques become paramount to safeguarding against these attackers, and having stringent access controls also is of high importance.
Where Does Netskope Come In?
Now we understand the threat landscape from the perspective of the attackers, their motivations and methods of attack from the perspective of the public sector, we will now look into where Netskope can be utilised to protect against these threats and the tools it brings along to benefit the public sector. The following tools can be integrated into your environment by adding their functionality to your Netskope policy stack, which is how netskope rules are applied to your environment.
Netskope's Tooling:
Netskope DLP:
Across the previous section there has been mention of how strong DLP techniques can go to prevent the attackers from fulfilling their goal. This is an area in which Netskope excels, whilst DLP is a facility in netskope which can be applied across much of its tooling. As such, when looking at a full integration of netskope you will, in a lot of cases, be introducing some aspect of DLP. You can also introduce to the policy stack specific DLP policies, an example of which could be looking at setting a rule which scans documents which are being exfiltrated from storage applications and prevents any from leaving which have GDPR information. This can also be done with images, for instance if you did not want images of ID cards to be downloaded from cloud storage. To enable this Netskope allows you to upload a ‘fingerprint’, which is an image template of the same type you don’t want exfiltrated, to which it can compare images being downloaded, blocking any which are too similar to the template. These methods, and the tools which will be mentioned later in this section all work towards providing to the users of Netskope, the facilities to prevent data loss.
Phishing Prevention and Protection:
Not so much a single tool but more a combination of tools used towards the end of preventing phishing from being successful. In Netskope this can be done through engaging Netskope’s NG-SWG and employing a URL filtering policy to block recognized phishing and scam sites. Along with a threat protection policy that inspects all web content to detect new phishing and scam sites using a blend of signatures, threat intelligence, and machine learning. Also, as Netskope and its knowledge base of risky websites and email URLs is constantly evolving, this combination becomes a solid way of mitigating and preventing phishing. Moreover, Netskope’s ethos of educating its users shines through in the handling of phishing attacks, as when a user is blocked from accessing a phishing url or a email is handled by Netskope, templates can be used on the pop up which appears for the user to explain exactly what has happened. All of this to the end of making sure that it does not happen again.
Netskope Reverse Proxy:
The Netskope reverse proxy capability can be leveraged to protect internal resources from those wishing to exfiltrate them when logging in on an unmanaged device, this could be used to thwart attacks by insiders with accounts or attackers who have obtained credentials. This works by the original publisher of the application handing over to Netskope who now served us our access to the Google app hence the redirect in the URL. As Netskope is now in line with our activity in the application, it can enforce the same policies for this specific application as if we have a client running on our machine.
The image below shows the change in the URL when Netskope is running the app through reverse proxy.
For the main three use cases mentioned in the previous section this becomes an invaluable tool for defending against attack as protection policies can be enforced on resources regardless of whether the attacker's device is managed or not.
ZTNA/Private Access: A key network tool which presents the opportunity to handle the aforementioned malicious attackers and also can provide more security when regarding the two other key threats would be Netskope Private Access or ZTNA. As can be seen in the image below, private access is a modern remote access service that fans out to enable access to applications in multiple networks, both in the public cloud and in managed data centres. And also provides zero trust application level access instead of network access with lateral movement.
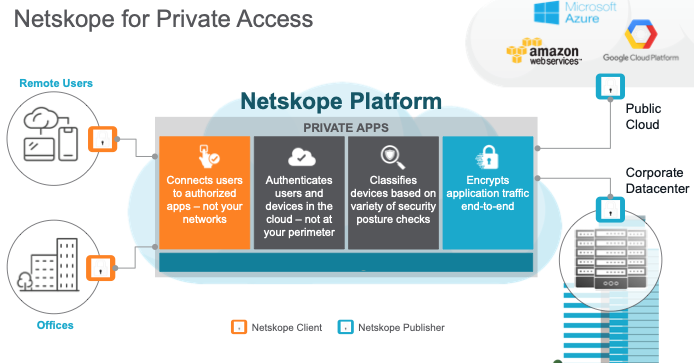
The benefits this provides to the public sector are such that resources can be accessed by authorised machines and users, but only for the need they have. Essentially limiting any lateral movement as much as possible and ensuring that attacks cannot be deployed across resources as they usually would be able to where something like a conventional VPN is used.
Conclusion
In conclusion, the public sector's vast and sensitive data landscape and unique position in governmental procedure makes it a prime target for a diverse range of cyber threats, from financially motivated attacks to politically driven disruptions. Given these risks, it's crucial for public sector organisations to employ robust and adaptive security solutions. Netskope’s comprehensive platform stands out by offering a multi-layered defence strategy tailored to these unique challenges. Through its advanced DLP policies, URL filtering, and threat protection capabilities, Netskope not only blocks known threats but also adapts to emerging ones. The use of its reverse proxy and ZTNA features ensures that both internal and external access are tightly controlled and monitored, reducing the risk of data exfiltration and unauthorised access. By leveraging Netskope’s solutions, public sector entities can enhance their security posture, safeguard sensitive information, and mitigate potential risks from various types of attackers. Ultimately, this proactive approach not only protects critical infrastructure but also reinforces the trust and reliability essential to public sector operations. As cyber threats continue to evolve, embracing a sophisticated and adaptive security solution like Netskope's is a vital step toward ensuring resilient and secure public sector services.







