
Why is Cloud Visibility Important?
Author: Jake Hammacott
Release Date: 09/01/2025
What is Cloud Visibility?
Cloud Visibility is the ability for an organisation to assess and monitor cloud resources. From the actual infrastructure being run in the cloud, how resources are used and changed by processes and users, to the actual cost and resources being expended to support all cloud activity. This can be particularly tricky when compared to on-premise infrastructure because cloud computing & Infrastructure is incredibly versatile: resources can be created, deleted and modified with little hassle, making scaling up, or down, production infrastructure extremely common. With this constant change that cloud vendors promote, tracking metrics and logs can be a difficult challenge to handle - with different cloud vendors using different logging methods, even at the cloud-app level.
Furthermore, to ensure optimum security processes are implemented into cloud infrastructure, cloud visibility must be applied at an optimum level. Cloud visibility is crucial in cybersecurity as it provides organisations with a clear understanding of their cloud infrastructure, data flows and activities. Without visibility, companies risk missing potential security threats, such as unauthorised access, data breaches or misconfigurations.
Effective cloud visibility enables and promotes monitoring, threat detection and compliance enforcement across cloud environments - helping to identify vulnerabilities, respond to security incidents and enforce policies consistently across relevant resources and identities. With many cloud vendors subscribing to the “Shared responsibility model”, where the cloud provider is responsible for ensuring that the underlying infrastructure is secured and protected from threats whilst the organisation utilising the cloud platform is responsible for the securing all data and applications housed, many complicated configurations can be often overlooked that wouldn’t be apparent in an on-premise environment.
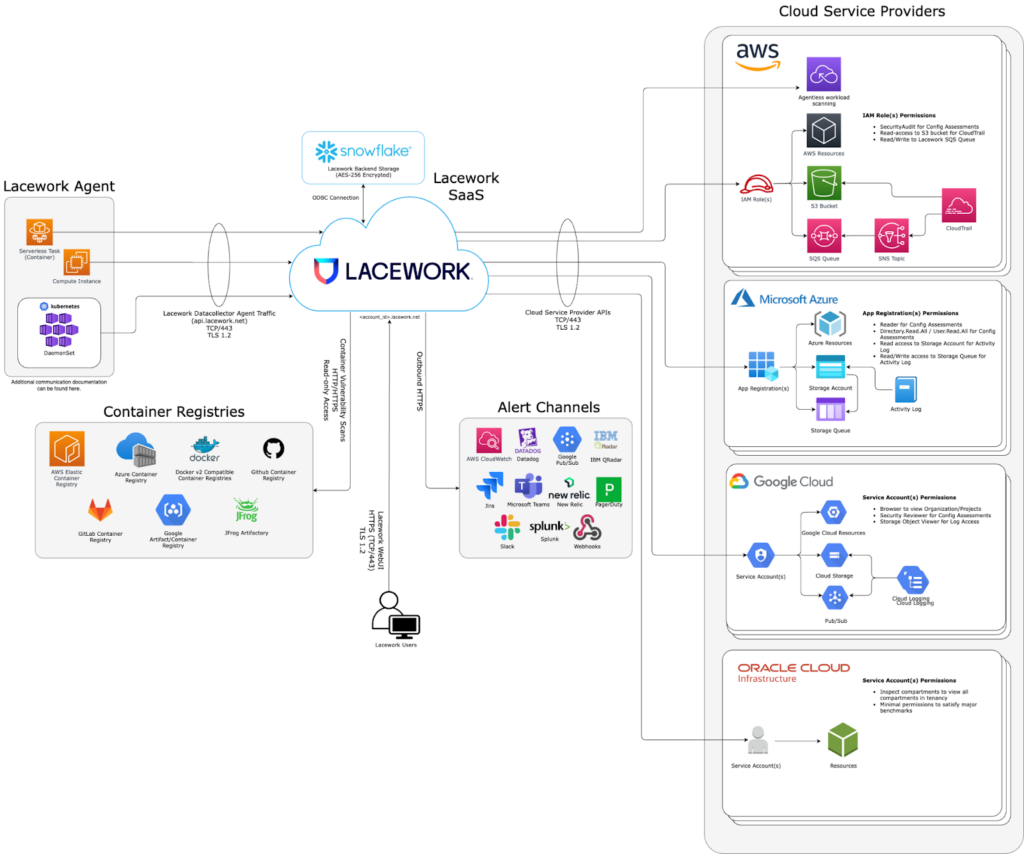
Lacework FortiCNAPP and Cloud Visibility
As a cloud-Native application protection platform (CNAPP), Lacework FortiCNAPP excels in bringing visibility into cloud environments, supporting Hybrid, Private and Public cloud solutions. Lacework FortiCNAPP’s main value comes from the lightweight integrations it offers into cloud accounts and resources. Lacework FortiCNAPP integrations range in functionality and applicability:
• Agentless integrations: incredibly lightweight workload scanning that integrates into cloud accounts to provide immediate insight into vulnerabilities, misconfigurations and secrets stored within the cloud - without the need to install agents into key resources.
• Agent-based: agents provide key data and analysis on application, host and user behaviours whilst requiring minimal system resources. Lacework FortiCNAPP’s agents are simple, flexible and self-contained - meaning they have very few dependencies and act almost independently from the rest of the cloud environment.
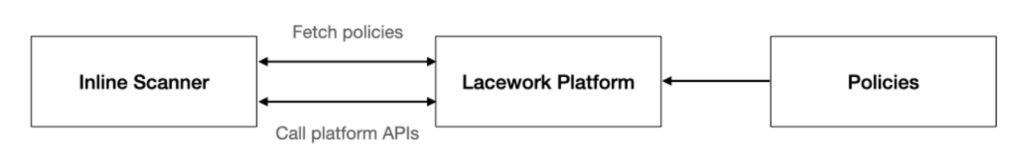
• Inline scanning: providing the option to identify misconfigurations before they hit production environments, Lacework FortiCNAPP’s in-line scanning sits within the DevOps CI/CD pipeline to alert on risky configurations and suggest recommendations to remediate issues by utilising out-of-the-box policies that are designed against many industry-recognised compliance frameworks (whilst also supporting the development and utilisation of custom policies). This provides a unique & valuable solution to tackling compliance violations, as identifying and remediating misconfigurations requires much less time, effort and budget to complete whilst still in the DevOps pipeline - as opposed to misconfigurations found in a live, production environment.
With Lacework FortiCNAPP fitting into and supporting most, if not all, cloud environments - compliance and vulnerability management becomes much easier to complete. With complete visibility into all integrated cloud accounts, attack paths - that malicious actors could exploit to execute an attack on key resources - can be identified and remediated. Lacework FortiCNAPP, additionally, provides remediations for all misconfigurations that fail against any policy enforced against the infrastructure.
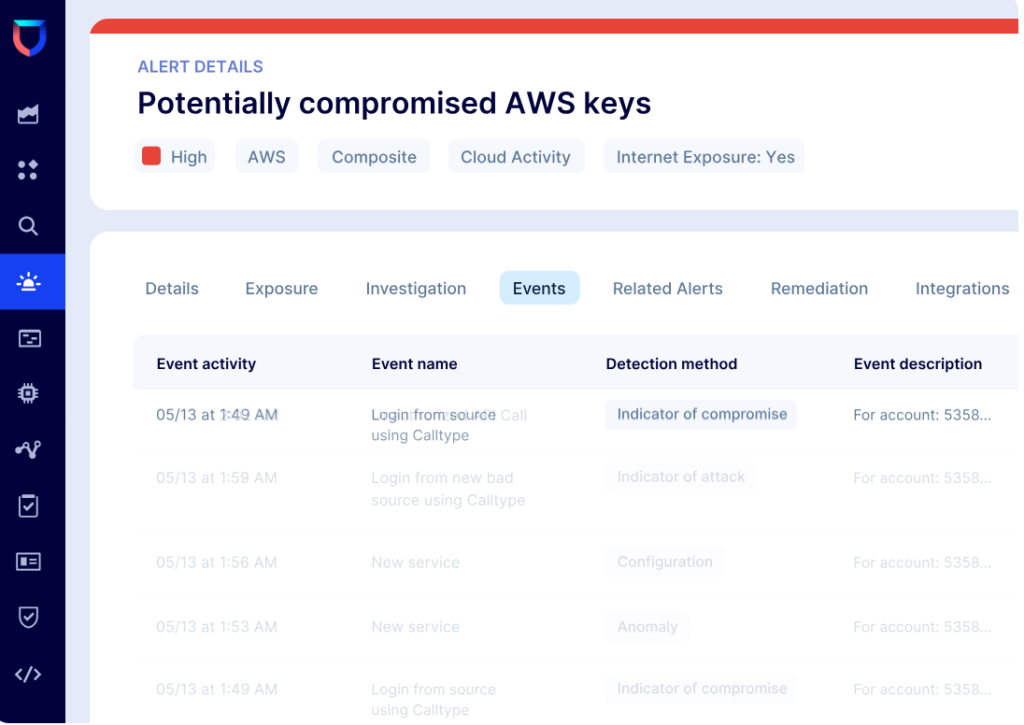
Additionally, a common issue larger cloud environments have is that, when housing many custom roles, groups and users, permissions are often set at the time of creation and then left untouched - regardless of changing responsibilities and requirements. This often leads to users having highly privileged accounts when only actually requiring and utilising a fraction of the permissions inherited to them.
From a cybersecurity perspective, this can cause and create risk. If a user that has full admin access to an entire cloud account becomes compromised, the scope of what a malicious actor could execute becomes massive. If the same user becomes compromised, but Lacework FortiCNAPP’s Entitlements tool has been utilised to revoke permissions on the user that they no longer actively require in their role, the impact any malicious activity would have on the cloud estate becomes dramatically reduced. Going through the process of permission & identity utilisation can be incredibly taxing when done manually, Lacework FortiCNAPP’s Entitlements solution tackles this by providing reports on risky users, groups and roles - completing most of the heavy lifting.
Netskope and Cloud Visibility
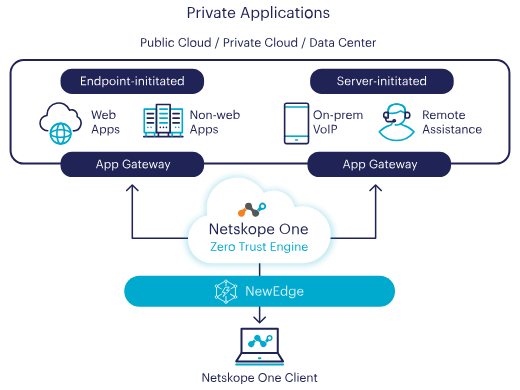
Whilst many Cyber Security and cloud visibility solutions offer “reactive” solutions to help identify risk and protect sensitive resources, Netskope aims to provide cloud Visibility through the actions taken by end-users and processes in order to mitigate and prevent harmful, dangerous or risky activity from ever being allowed in the first place. Netskope utilises a tenant that is deployed onto endpoints to inspect, analyse and alert on network and system traffic.
With end-users onboarded into Netskope, policies can be enforced onto activity executed. In terms of cloud visibility, Netskope collates and analyses traffic coming to, going from and residing within your cloud Estate. Events can then be displayed ad-hoc (or exported into reports) to give a clearer picture into what activity users are attempting when interacting with the network. From this, large amounts of data can be analysed - allowing for policies to be developed that promote and enforce safe usage of key and external resources, spanning multiple functionalities and use-cases:
• NGSWG (Next-Gen Secure Web Gateway): filters (blocks, allows, redirects, asks for justification, etc.) web traffic, allowing organisations to implement policies that enforce safe-sage web fundamentals and prevents inappropriate, risky and dangerous activity from ever taking place.
• ZTNA (Zero-Trust Network Access): provides a modern solution to remote access and focuses heavily on the principles of Zero Trust.
• CASB (Cloud Access Security Broker): Netskope sits in between users and external resources, acting as a security policy enforcement point to prevent sensitive data leaving the organisation and harmful payloads entering the network.
• DLP (Data Loss Prevention): protects sensitive data from leaving trusted locations. DLP rules and policies can be configured using custom or out-of-the-box profiles that scan data leaving the network for sensitive information (i.e. GDPR or PCI data) and enforces a policy on the attempted transmission.
Netskope, ultimately, utilises cloud visibility to prevent malicious & dangerous activity from happening in the first place. All events and alerts are reported on, giving analysts a clear insight into risky behaviours and attempted attacks into the Network.
Wrapping Up
Cloud visibility is an incredibly important fundamental that must be applied to any cloud-based organisation. Not only does it provide an insight into resource utilisation, running costs and infrastructure, but it also empowers organisations to utilise data generated to its fullest in the cyber security sector. Tools and solutions can take on a lot of the burden often encountered with cloud visibility, allowing analysts to focus on what’s important: identifying and remediating true positive incidents, violations and risks. Both Lacework FortiCNAPP and Netskope promote cloud visibility within the context of security but approach challenges and solutions in completely different ways.







