What Does Splunk Attack Analyzer Do?
Author: Jake Hammacott
Release Date: 24/02/2025
In the contemporary digital landscape, malicious actors and adversaries are continuously evolving their tactics, techniques, and procedures (TTPs). They relentlessly innovate and devise increasingly sophisticated attacks aimed at circumventing the security measures implemented by legitimate organisations. These attacks can take various forms, including malware, ransomware, DDoS attacks, and zero-day exploits, among others. The constant evolution of these threats underscores the critical importance of robust and adaptive cybersecurity defences for all organisations, regardless of their size or industry.
However, the most common form of cyber-attacks rely on social engineering tactics, with phishing being a prime example - encompassing over 70% of all cyber attacks. Phishing attacks often use deceptive emails, websites, or messages to trick individuals into divulging sensitive information, such as login credentials, personal data, or financial details. These attacks can be highly targeted, with attackers carefully crafting their messages to appear legitimate and exploit the recipient's trust.
Even with a strong cybersecurity culture and employee awareness programs, which are vital in defending against phishing and social engineering attacks, the responsibility of analysing potential threats reported by users still rests on the shoulders of the security analyst. This can be a time-consuming and resource-intensive task, especially given the sheer volume of potential threats that need to be investigated.
The analyst must carefully examine each report, determine its credibility, and assess the potential risk it poses to the organization. This requires access to the right tools and technologies, which often span multiple solutions - leading to a team that is required to waste time and resources attempting to mitigate tool sprawl with solutions that may not integrate easily together and dedicate additional effort into investigating and remediating cases & incidents.
Introducing Attack Analyzer
Attack Analyzer streamlines the investigative process by automating a substantial portion of the tasks typically undertaken by a security analyst. This automation allows analysts to focus on higher-level decision-making and threat mitigation, rather than getting bogged down in repetitive and time-consuming manual tasks. Attack Analyzer takes submissions - from either the Web UI, email or API integrations - and automatically creates dedicated jobs where its internal (and externally integrated) engines take on engine-specific tasks in an effort to identify malicious, risky or suspicious activity or functionality. If new resources are discovered during any of these tasks, Attack Analyzer’s engines then run new tasks on this resource until it is confident that no new resources have been discovered. Once all resources have been analysed and all detections have been documented, results are available in a fully-normalised format - making it incredibly easy for analysts to pick up and make immediate, actionable decisions, speeding up remediation times drastically.
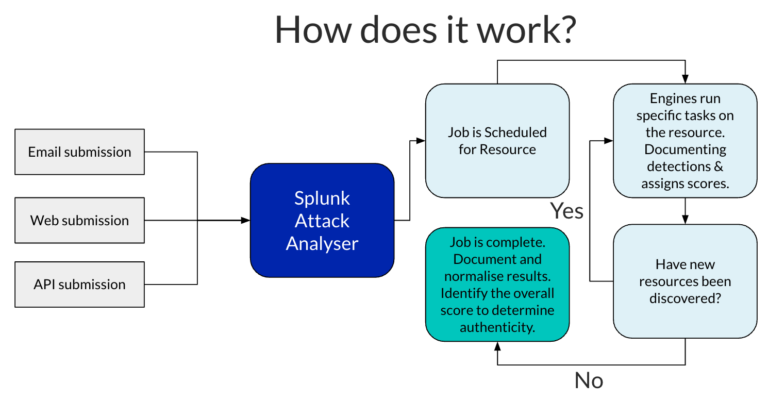
Attack Analyzer uses a particular set of vocabulary when referencing internal processes, functions and utilities:
Resource: All items submitted to SAA are considered resources. Additional resources may be identified during analysis which can be added to the original for further investigation.
Job: Created once a resource has been uploaded to SAA. It contains analysis of investigations executed on the resource and other resources identified during the original analysis. Each job has a unique ID.
Engine: A microservice specialising in processing specific items. A job contains one or more engines. An engine is associated with a defined set of analysis tasks.
Task: A specific run of an engine for a specific resource.
Normalized Forensics: A forensic format all analysis is normalised to after analysis has completed.
Raw Forensics: All fields returned by the engine in the engine specific format.
Score: Some engines generate scores based on results. Determined by adding up the score of each engine, the highest score of a job is promoted to the overall score with 100 being the max and 0 the minimum.
Attack Analyzer drastically increases the speed of investigation. By logically working through each resource and dedicating relevant engines to solve specific tasks, out-of-the-box, Splunk Attack Analyzer comes with 10 engines (whilst providing the opportunity for you to integrate your own if necessary):
URL Reputation: Checks URLs and Domains against various 3rd party data feeds to determine whether they have previously been used to host malicious content.
Web Analyzer: An automated Web browser that accesses and navigates through websites to analyze web pages. Web traffic is then stored as HAR archives or PCAP files for further analysis.
Archive Extraction: Exclusively works on extracting data from archives, utilising data from other sources (Advanced Web Submissions, Email Analyzer, built-in Brute force list, etc.) to obtain and crack password protected files, before passing the data onto other engines.
ClamAV: Returns signatures and designates them a score, depending on matched detections on known malicious content.
Email Analyzer: Screenshots emails and extracts all relevant data to run detections against, including the message headers, text and any attachments or URLs. Malicious or suspicious content, usually relating to social engineering tactics/techniques, is reported in the detections.
Windows 7 & 10 Sandboxes: Full Operating Systems that act automatically to detonate suspicious files in a dynamic environment. Also allow for the opportunity for analysts to spin-up their own sessions to promote safe, hands-on investigation in a remote environment.
Static Doc Analysis: Analyses documents, HTML, images and scripts to identify malicious content and phished brands. Metadata about the document is extracted and sent to the Attack Analyzer, along with URLs converted from QR codes, images, etc.
Static File Analysis: Analyses files, reporting and returning important information, such as: file size, EXIF metadata, common hashes and PE data (if the file is a Windows file). This engine also utilises Machine Learning to score and determine the threat of executable files. CAPA analysis is also used against executable files to determine the capabilities of the file, which is then mapped against MITRE ATT&CK tactics and techniques.
YARA: Scans files against set YARA rules created by Splunk Attack Analyzer and returns detection based on rule matches against the file. You can implement your own, additional YARA rules into the ruleset.
Splunk Attack Analyzer in Action
By using all of these engines within one single solution, the speed of investigation completion becomes immediately evident. In the following example, an attacker has attempted to compromise an end-users credentials and drop trojan malware onto their workstation. The initial email included a password protected PDF file that the attacker wanted the target to open.
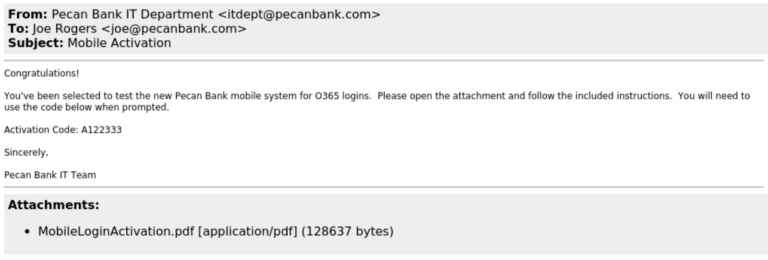
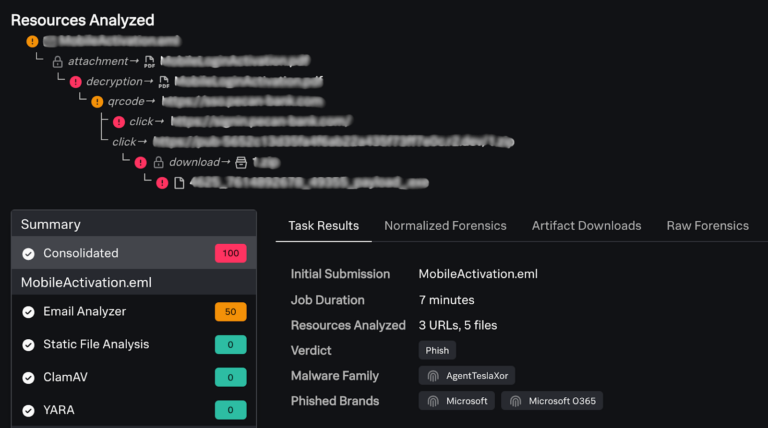
From there, by utilising the Archive Extractor in tandem with the Email Analyzer, Attack Analyzer was able to download and decrypt the file by utilising the “Activation Code” found in the original email, automatically and without human intervention.
Once opened, Attack Analyzer then had to navigate through a QR Code (which I won’t share on this blog as it leads to live malware!), pointing towards a new URL containing a link to a fake Microsoft O365 login page - used for credential harvesting - and a link to download Trojan Spyware which would automatically deploy itself on, and infect a system once unzipped.
Navigating through this entire attack requires access to and the investigation of 3 URLs and 5 files. For more traditional tools and approaches, it may take an analyst 30 - 45minutes to gain a decent understanding of what’s happening and what makes this attack so deadly. However, from the point that the original email was reported and received by Splunk Attack Analyzer, the entire job was completed in 7 minutes - without requiring human input at any point of the investigation. In those 7 minutes, all 10 out-of-the-box engines were utilised, culminating to 55 detections that granularly document the functionality and workflow of this attack.
Conclusion
Splunk Attack Analyzer significantly boosts the efficiency and effectiveness of security operations by automating the investigation of cyberattacks, including malware and phishing attempts. This automation frees security analysts and SOC technicians from repetitive and time-consuming tasks, allowing them to focus on higher-level activities such as remediation and incident resolution.
By taking on the burden of initial investigation and documentation, Splunk Attack Analyzer streamlines the entire incident response process. Security teams can rely on the tool to automatically analyse potential threats, gather evidence, and generate comprehensive reports. This not only saves time and resources but also ensures that potential threats are identified and addressed quickly, minimising the potential for damage.
With Splunk Attack Analyzer, security teams can move directly from alert to action, bypassing the need for extensive manual investigation. This allows them to respond to threats more rapidly and effectively, ultimately improving their organiaation's overall security posture.