
Why Are ZTNAs Replacing Traditional VPNs?
Author: Ben Norcutt
Release Date: 27/03/2025
In today’s evolving cybersecurity landscape, traditional Virtual Private Networks (VPNs) are increasingly being replaced by Zero Trust Network Access (ZTNA) solutions. As organisations shift to remote and hybrid work models, securing remote access efficiently and effectively has become a top priority. But what exactly is ZTNA, and how does it compare to the familiar VPN? Let’s explore.
Understanding ZTNA
Zero Trust Network Access (ZTNA) is a security framework that enforces strict identity verification and access control before allowing users to connect to applications or resources. Unlike traditional VPNs, which grant broad access to an entire network, ZTNA operates on a least-privilege principle, ensuring users can only access the specific applications they need based on predefined security policies.
Why Replace VPNs with ZTNA?
VPNs have long been the go-to solution for remote access. However, they come with several limitations that make them less ideal in today’s cloud-first and security-conscious environment.
1. Security Risks of VPNs
VPNs create an encrypted tunnel between a remote user and the organization’s network. While this is effective for securing data in transit, VPNs often grant users excessive network access. A compromised VPN credential can expose an entire corporate network to cyber threats, increasing the attack surface for ransomware, phishing, and insider threats.
2. Lack of Granular Access Control
VPNs generally provide an “all-or-nothing” approach. Once a user connects, they often have broad access, making it difficult to enforce least-privilege access. ZTNA, on the other hand, ensures users only access the specific applications they need without exposing the entire network.
3. Cloud and SaaS Compatibility
Many modern businesses rely on cloud applications and Software-as-a-Service (SaaS) solutions. Traditional VPNs are designed for network access rather than application-specific access, making them inefficient for cloud environments. ZTNA, by contrast, provides direct-to-application access, bypassing the need for network-wide connectivity.
4. Performance and Scalability
VPNs often struggle with performance issues, especially as businesses scale. The need for centralized VPN gateways can create bandwidth bottlenecks, leading to slow and unreliable connections. ZTNA solutions use a more distributed approach, offering seamless and optimized access to applications without overloading central infrastructure.
5. User Experience and Flexibility
VPNs require client software installation and manual connections, which can be cumbersome for users. ZTNA solutions, often cloud-native, provide smoother and more flexible access experiences without requiring constant VPN client management.
How ZTNA Works
Netskope defines Zero Trust simply as a security model based on the premise that no one should be blindly trusted inside the network or allowed access to resources, applications, or data until they have been validated as a legitimate user/entity with a legitimate need to access the information/data.
Netskope employs Zero Trust as an operation concept to the services provided as part of the secure access service edge (SASE) architecture built on the Netskope NewEdge network. This data-centric design allows for maximum interoperability across all applications while enforcing trust based on context, at the network, application, and user level, irrespective of a user's location or access method.
Here’s how it typically works:
1. User Authentication - The user logs in using multi-factor authentication (MFA) or Single Sign-On (SSO).
2. Device Security Check – The system verifies that the user’s device meets security compliance requirements (e.g., updated OS, antivirus software, etc.).
3. Application-Level Access – Instead of providing network-wide access, ZTNA allows the user to connect only to the required applications.
4. Continuous Monitoring – Unlike a VPN, which assumes trust after authentication, ZTNA continuously monitors behaviour to detect anomalies and revoke access.
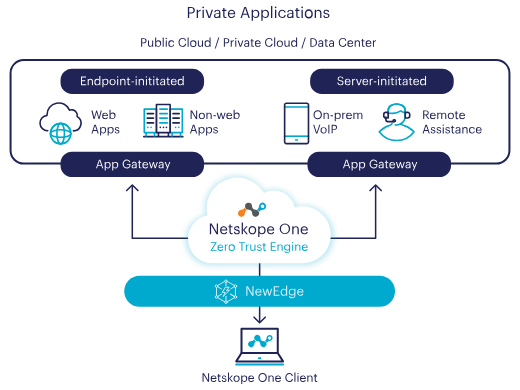
ZTNA Adoption: Key Considerations
Transitioning from VPN to ZTNA requires a strategic approach. Here are some key factors to consider:
• Assess Existing Infrastructure – Identify which applications and resources need secure access.
• Adopt Identity and Access Management (IAM) – Implement strong IAM policies, including MFA and least-privilege principles.
• Integrate with Cloud Security – Ensure that ZTNA solutions work well with cloud services and hybrid environments.
• Educate End-Users – Train employees on new access methods and security best practices.
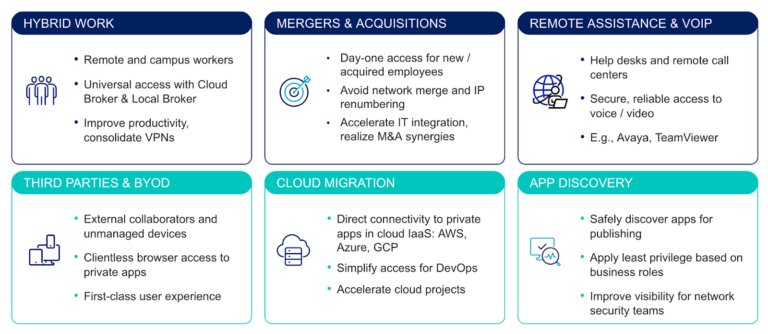
Use Cases for Netskope Private Access (ZTNA)
Netskope Private Access (ZTNA) Architecture
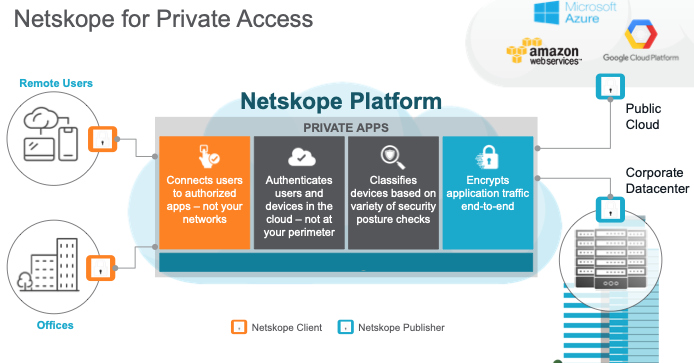
Remote or local users have the Netskope One client installed on their machines to facilitate seamless access to applications irrespective of their location, local or cloud based applications.Connectivity to the application is managed by the Netskope publisher, a lightweight linux based computer resource.
A secure tunnel is established outbound from the client to the Netskope New Edge network and outbound from the publisher to the Netskope New Edge network requiring no inbound IP holes to be created in corporate perimeter firewalls.
A user is allowed access to their applications by the real time policy created in the Netskope UI.







