Lacework FortiCNAPP: A Data-Driven Security Platform for the Cloud
Author: Jack Hancox
Release Date: 27/03/2024
In the dynamic landscape of cloud computing, ensuring the security of your digital assets is paramount. As organisations migrate to cloud environments, a robust security solution becomes crucial. Enter Lacework FortiCNAPP, a cutting-edge data-driven security platform tailored for the cloud.
Lacework FortiCNAPP in a Nutshell
Lacework FortiCNAPP is not just another security tool; it's a comprehensive solution specifically designed for cloud environments. This tool offers a suite of features that collectively provide continual and unparalleled visibility, threat detection, and proactive security measures for your cloud estate.
Key Features
1. Container Security
Lacework FortiCNAPP provides complete visibility into the security of your containers, allowing you to ensure they are locked down and have as small a potential attack surface as possible.
2. Vulnerability Identification
Lacework FortiCNAPP enables users to evaluate, detect, and report vulnerabilities present on hosts, containers, and pods within their environment. This allows for the identification and proactive management of software vulnerabilities.
3. Cloud Estate Visibility
Gain a bird's-eye view of your Cloud resources, from servers to containers and applications. Lacework FortiCNAPP provides a detailed breakdown of your cloud estate, offering insights into the intricacies of your Cloud infrastructure.
4. CloudTrail Logs
Harnessing the power of AWS CloudTrail logs, Lacework FortiCNAPP captures and analyses activities within your AWS environment. From user logins to API calls and error tracking, Lacework FortiCNAPP keeps a vigilant eye on your cloud operations.
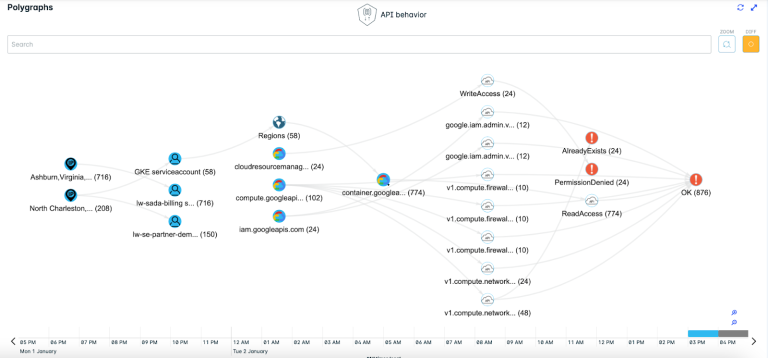
5. Polygraph: Visualising Communication
A standout feature of Lacework FortiCNAPP is the Polygraph. This visual mapping tool creates a clear representation of communication flows and dependencies within your cloud infrastructure. It simplifies the complex task of understanding how various components interact with each other.
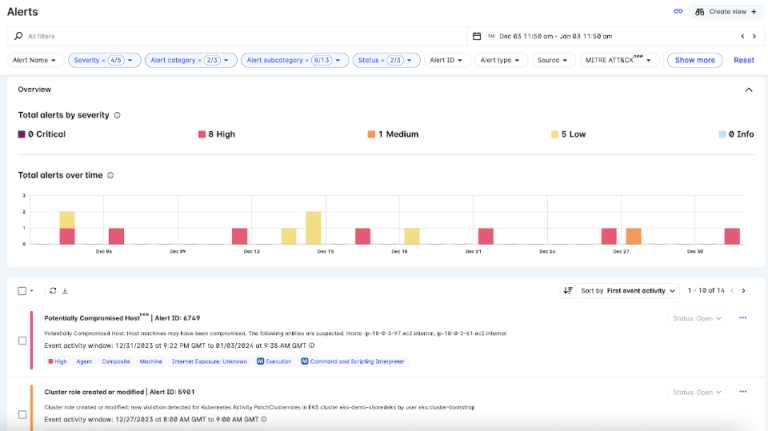
Event Analysis
Lacework FortiCNAPP’s Event Analysis helps organisations recognise and address potential security threats and vulnerabilities before they have a chance to disrupt business operations. This is split into two parts:
1. Alerts and Notifications
Lacework FortiCNAPP goes beyond passive monitoring; it actively generates alerts for potential security issues or anomalies. This proactive approach ensures that you are promptly informed about any suspicious activities within your cloud environment. It is equipped with a plethora of alert rules straight out of the box, and these are typically divided into configuration, anomaly, and user activity alerts. Lacework FortiCNAPP actively learns from typical cloud behaviour using machine learning to alert on activity or changes that aren't typically found in an organisation's standard business activity. This ultimately aims to reduce alert noise and spot activity that typical rule-based alerting wouldn't necessarily pick up without a large amount of alert rules.
2. Detailed Event Analysis
The tool offers a deep dive into specific events, unravelling the "who, what, where, when, and why" of each occurrence. An example of this would be the analysis of an external connection, providing a detailed breakdown of the event and steps for investigation.
Integrity Monitoring
Lacework FortiCNAPP includes integrity monitoring features, checking for changes in hashes and identifying any activities that may indicate unauthorised alterations. This layer of visibility facilitates deeper protection and ensures the integrity of your cloud resources.
Reports and Compliance
1. Policy Configuration
Users have the flexibility to configure policies, determining what Lacework FortiCNAPP reports on. This customisation allows organisations to align with specific compliance requirements and focus on what matters most to them.
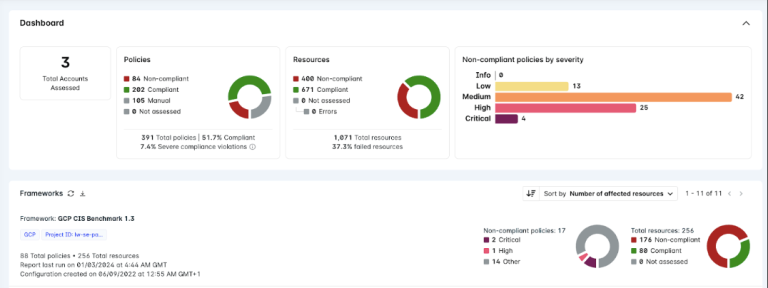
2. Detailed Reports
Lacework FortiCNAPP generates detailed reports on compliance standards, such as the CIS Benchmark, offering insights into compliance levels and potential issues. These reports serve as valuable resources for organisations aiming to maintain a robust security posture, facilitating easier audits and providing concrete evidence of the company's commitment to cybersecurity best practices.
Integration and Ease of Use
1. Seamless Cloud Platform Integration
Lacework FortiCNAPP seamlessly integrates with cloud platforms, with a particular emphasis on AWS. The setup process is straightforward, and Lacework's documentation provides clear guidance, making integration a breeze.
2. Agent Deployment
Deploying agents is a hassle-free process. Lacework FortiCNAPP ensures a smooth integration with agents, facilitating the establishment of trust between the agent and your cloud environment.
Prevention and DevOps Integration
Lacework FortiCNAPP positions itself as a proactive security solution. By integrating seamlessly with DevOps processes, it identifies potential issues early in the development pipeline, preventing security lapses before they occur. Moreover, Lacework FortiCNAPP goes beyond detection by incorporating Infrastructure as Code (IAC) within its framework. This innovative approach empowers developers by providing a secure foundation without impeding their workflow, ensuring that security is seamlessly woven into the fabric of the development lifecycle. This proactive stance not only fortifies the entire development process but also mitigates potential threats before they materialise, offering a comprehensive and preemptive security solution for modern applications.
Conclusion
In conclusion, Lacework FortiCNAPP is more than just a security tool – it's a sentinel for your cloud infrastructure, offering unparalleled visibility, proactive threat detection, and a robust set of features. Lacework FortiCNAPP stands at the forefront of data-driven security platforms tailored for the cloud.
As organisations navigate the complexities of cloud security, Lacework FortiCNAPP emerges as a valuable ally, ensuring that your digital assets remain secure, compliant, and resilient in the face of evolving threats.