What is Attack Path Analysis?
Author: Jake Hammacott
Release Date: 17/06/2024
Attack path analysis is a generic term used for solutions that attempt to link and visualise risky assets that could be exploited in tandem to progress the state of a cyber-attack. The purpose of this is to enrich compliance, vulnerability and entitlement findings with clear paths that lead to, or expand on, a specific exploitation that your infrastructure is currently susceptible to. In this blog, we’ll be going over attack path analysis fundamentals and showing how Lacework FortiCNAPP takes this concept and further develops it to provide additional value to compliance and vulnerability findings.
The Issue with Compliance & Vulnerability Reporting
Traditional reporting on non-compliance and vulnerability scans aim to produce mass amounts of data utilising every resource scanned. This can be incredibly beneficial when it comes to showing the individual biggest risk or risks that are common amongst many resources.
However, this can also cause issues in the modern world, with compliance and vulnerability reports providing too many individual records, analysts can often find it difficult to establish links between different insecurities found in your cloud infrastructure. For example, the following shows a Lacework FortiCNAPP vulnerability table, where each record reflects an individual host:
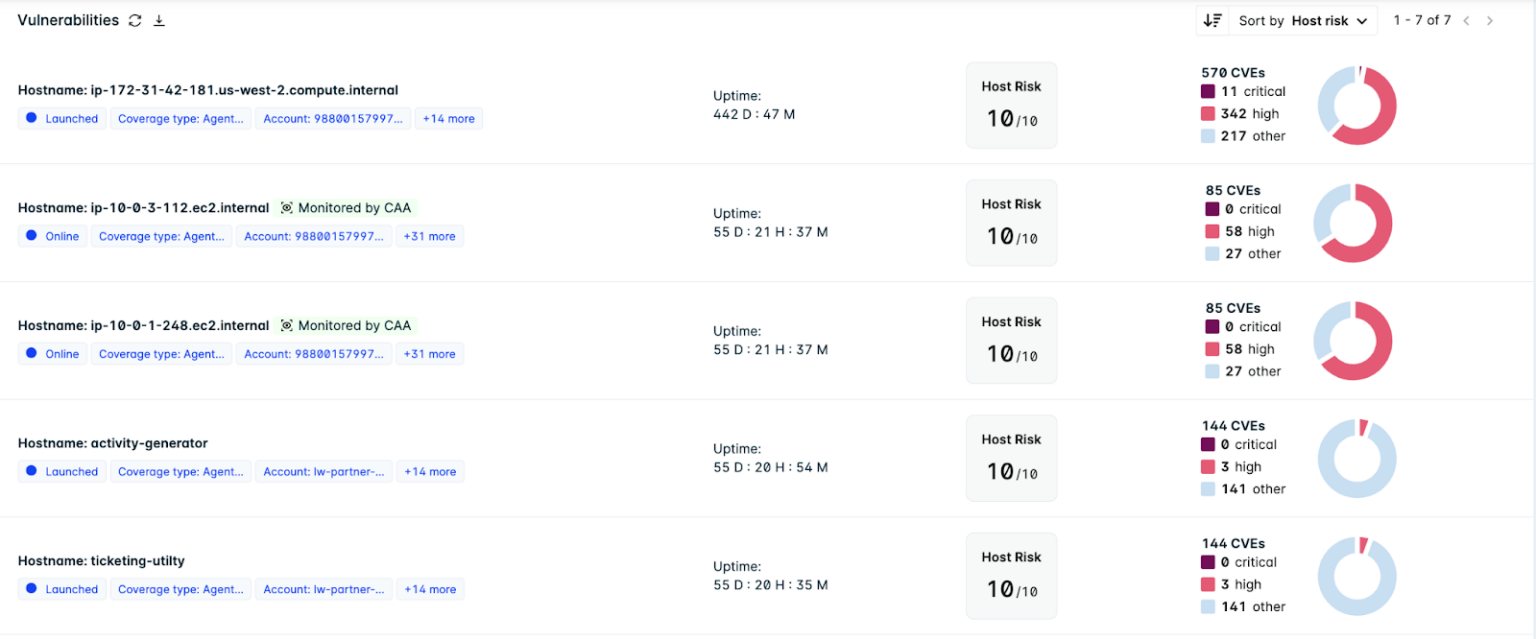
A table like this is great for certain use-cases and situations. If you’re looking at finding the top risky assets you currently house, Lacework FortiCNAPP can allow you to identify which hosts have the highest vulnerability scores and allow you to drill down and find individual insecure applications or resources within the host that need patching, upgrading or removing - to make the machine more secure. However, if a specific vulnerability has been researched and deemed an acceptable risk, analysts may want to drill into the machine and identify if this vulnerability can be leveraged by exploiting other machine’s insecurities to move laterally through the network. Just because a machine is buried deep inside your cloud network, it does not mean that malicious actors won’t be able to exploit vulnerabilities found on it.
What is Attack Path Analysis?
Knowing that a critical vulnerability is active on an internal machine sounds problematic, but without knowing how that machine interacts with the rest of the network, your security analysts may have a hard time identifying what true risk the vulnerability brings to your infrastructure and data. Attack path analysis is a method used to visualise and demonstrate paths malicious actors could take to access sensitive resources. It allows analysts to gain further insight into how a vulnerability or non-compliant configuration could be exploited to develop an attack from a threat actor.
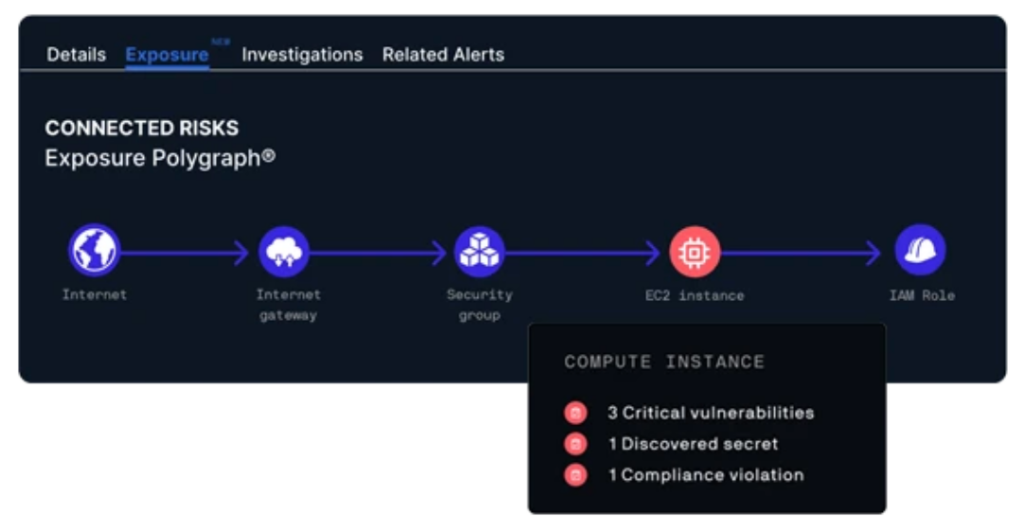
Lacework FortiCNAPP and Attack Path Analysis
Lacework FortiCNAPP’s attack path analysis dashboard empowers you to “Think like a hacker. Fix like an expert.” By utilising both agentless and agent-based ingestion methods configuration and vulnerability data, secrets scanning, activity data and runtime data can be analysed to create exposure polygraphs. This creates visualisations of potential attack chains to allow analysts to understand which resources could be targeted in an attack, along with the methods an attacker could use to reach them.
Within Lacework FortiCNAPP’s attack path analysis dashboard, an exposure polygraph is available for each scanned path. Additionally, details on all resources within the path are listed to provide analysts with all the context they need to fully understand the path an attacker could take, including:
• Machine Details: an overview of the core information of the machine (i.e. IP address, hostname, etc.)
• Vulnerabilities: a detailed table showing all scanned vulnerabilities of the specific machine, showing package name, severity, CVSS score, the current version of the package and the version of the package that will fix the vulnerability
• Secrets: a table documenting exposed secrets found on the machine. For instance, an exposed ssh private key
• Compliance Violations: a list of all non-compliant configurations along with a description of the policy and a severity
• Users: multiple tables documenting failed login attempts, user activity and user authentication
• Exposed ports: as you would expect, a list of exposed ports and additional details on them, including application, protocol and machine information
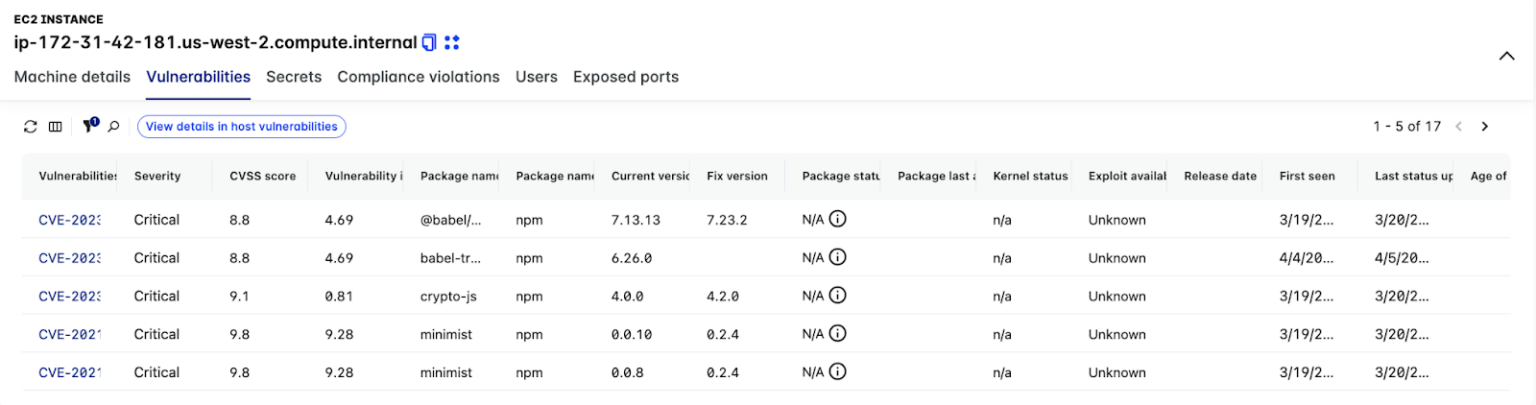
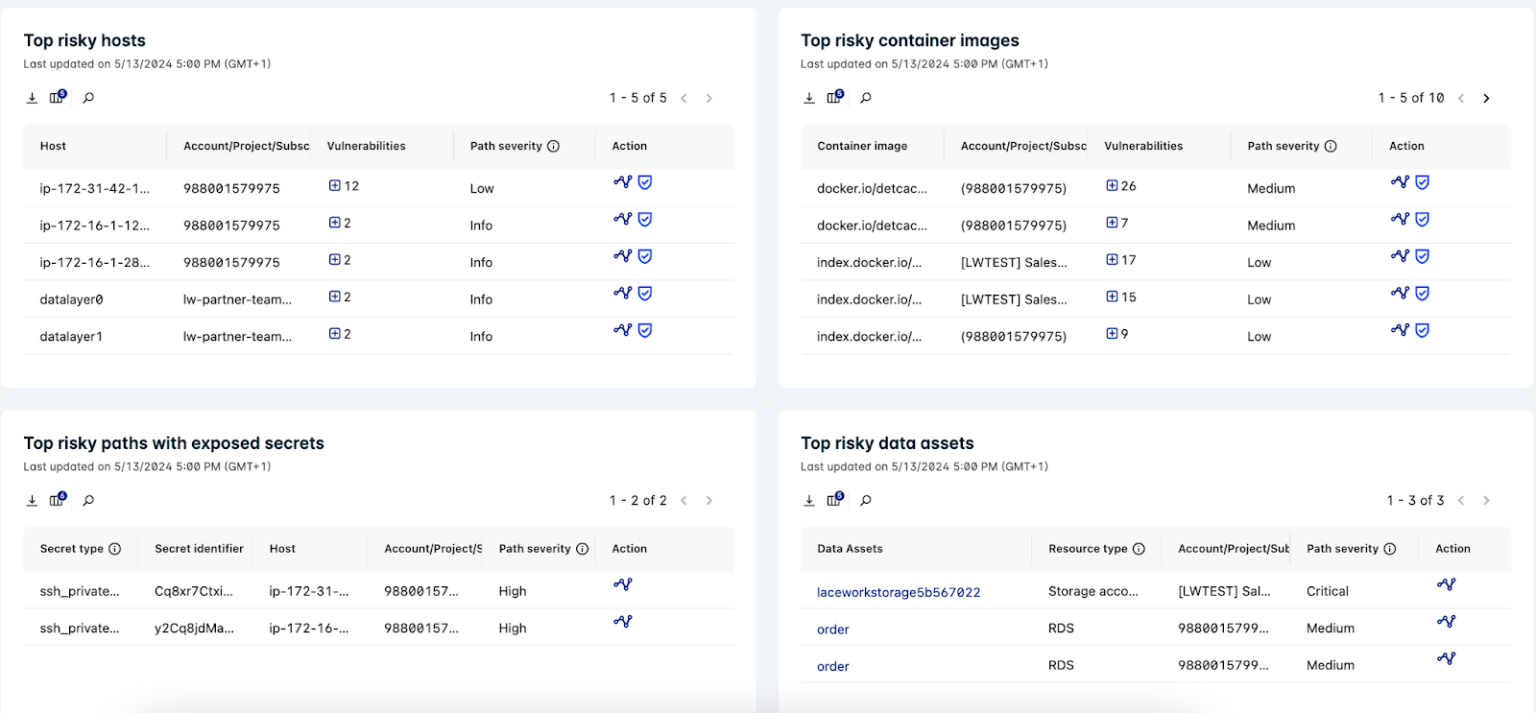
Before even accessing an attack path, the attack path analysis dashboard lists all risky assets found, with individual focuses on hosts, container images, data assets, entitlements and exposed secrets. This allows analysts to prioritise working on attack paths that bring the highest amount of risk to your organisation. With this approach, their time and work becomes more valuable and efficient, by eliminating the time it would take to obtain the context needed when looking at more traditional compliance and vulnerability reports. Within Lacework FortiCNAPP’s attack path analysis dashboard, an exposure polygraph is available for each scanned path. Additionally, details on all resources within the path are listed to provide analysts with all the context they need to fully understand the path an attacker could take, including:
Conclusion
The ultimate goal of attack path analysis is to provide the information analysts need to shut down and secure attack chains that malicious adversaries could exploit to obtain sensitive information or gain access to back-end devices or machines. Lacework FortiCNAPP takes this a step further, applying rich context and ranked attack paths to make dealing with compliance and vulnerabilities more efficient to your organisation.
More Resources like this one:
Lacework FortiCNAPP Attack Path Analysis with Jake Hammacott | Explainer Series - Episode #4
Key Capabilities from the Cloud Security Experts