
What is Public Cloud Security?
Author: Oliver Knapp
Release Date: 10/06/2024
In the modern cyber world it is exceedingly rare for an individual or company to not be in some way connected to a network, be that through using their mobile data, or being connected to broadband. As such it is commonplace to be connected to a public cloud, consuming resources, whether in the form of productivity or leisure. Due to the open nature of these clouds, there are grave inherent security risks to consider, a malicious user is able to gain access to the network much easier than a private network. In this blog we will discuss exactly what a public cloud is, alongside where and why they are used, we will look at the main threats to these clouds as well as the ways of securing them, and also take a dive into how we at Somerford can facilitate this.
What is a Public Cloud and how is it different?
The first key point to understand is what exactly is a public cloud and how does it differ to other types of cloud? A traditional cloud infrastructure utilises computing hardware, usually hosted by a third party or away from the consumer in order to provide on demand access to processing and data storage, with larger clouds having multiple data centres. These clouds are most commonly provided through cloud service providers such as Amazon and Microsoft. They typically require users to log on to consume the resources and can be managed by administrators, giving a high level of control - this is known as a private cloud.
A public cloud on the other hand, still retains the previously discussed architecture but the resources are open to anyone to virtually access, and for the most part are managed by a third party. An example of this would be streaming services such as Netflix, where anyone can pay for an account and gain access to the cloud in order to stream movies and shows.
Public clouds offer a few key benefits over their private counterparts, from a business perspective, there is the benefit that paying for and hosting a public cloud allows for your services and offerings to scale ad-hoc as the management side of things is not directly handled by you. Public cloud is usage based and as such, this also allows for costs to be kept on top of. Furthermore, the fact that the infrastructure is handled by a third party means that it will be reliable, maintained well and kept up to date. This also provides organisations the benefits of cost cutting due to not having to maintain, create and scale the architecture, gives you more time and less work costs when compared to a private cloud.
Public Cloud Security
The first consideration when looking at offering public cloud based services, should be the security of your customers, their data and the services being provided. This differs slightly from private cloud solutions as any back end security you would have had to cover, is out of your hands and is handled by the third party being utilised.
In essence, with a public cloud, the amount of security you have purview of is less, but the attack surface is greater and the risk is increased. This is due to the fact that an attacker can gain entry onto your systems, to some degree, with ease, the same way a normal user would. They can then attempt to laterally move through your systems or intercept data from a much more advantageous position than if they were to attempt to attack a private cloud. Not only this, but because of the nature of public clouds being widely accessed and as such a large amount of data is being put through them, they are much more enticing targets for would-be attackers.
This goes to show that there is a great need to ensure that yours and your customers' data is entirely secure. This is further backed up by statistics which, when combined, create quite a bleak overview for any company lacking when it comes to their public cloud security, as reported by Wall Street Journal in March 2024, 82% of data breaches were cloud based, with companies on average running half of their workload in public clouds, a massive security concern begins to form.
What are the threats?
The main threats to public clouds boil down to a few main categories:
• Data Loss/Exfiltration: This is the most common threat that would be experienced in a public cloud, with the inherent nature of these clouds being incredibly data centric, there is an increased threat of this data being exfiltrated. This is, as a whole, due to the previously mentioned large data attack surface and the lucrative opportunities for hackers. Whilst a large amount of this data is protected by the third party suppliers, not all of it is and even that which is is still at risk of attack - no system is ever 100% secure.
• Insider Threats: As with any cyber systems, anyone with access to sensitive data is a threat. This is a chief security concern amongst all cloud infrastructure and is no different here. There is typically a financial or malicious motive with these attacks, such as a disgruntled ex employee or an employee being made an offer of a large amount of money to give access or account details to attackers. However there is also the possibility of social engineering resulting in insider threats coming to fruition, which is another angle to watch for when looking at your public cloud security.
• Weak Security/Traditional Techniques:
Traditional hacker techniques are still prevalent in the modern world, be that brute force password attempts on an admin account, or something as simple as SQL injection. If your security isn’t sufficient, these attacks may end up being successful. This replicates also to your data security, if there isn’t a sufficient amount of security for data both at rest or in transit, then it could be stolen or monitored from right under your nose.
Securing your Public Cloud
As previously mentioned, whilst the security of the actual infrastructure within a public cloud is out of your hands and due to this, most of the time, would be pretty airtight, there are still considerations to be made when looking at the aforementioned security of a public cloud. In essence you would be responsible for all the security which is not infrastructure based, the diagram below should explain this better:
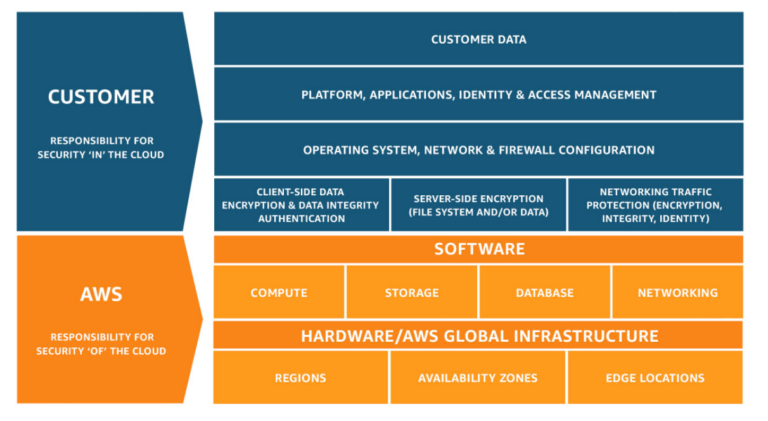
The best way to secure these clouds also can be categorised similar to how the threats were, that is, protecting against data loss and insider threats alongside securing the infrastructure that you do have purview over.
Protecting customer data, client side data and network traffic would usually come in the form of advanced encryption techniques, alongside strong traditional security such as firewalls and the use of IPS (intrusion prevention systems). Having an established SOC (security operations centre) is also another good way of monitoring and handling any threats to your data and network traffic in real time. Whilst there is no way of making data completely secure, you can put in measures which greatly reduce the threat of data loss and when or if this does occur, handle the events in the best and most efficient ways.
Malicious/monetary based insider threats are best prevented and defended against subtly. This is due to the fact that if you were to tell your employees that you do not trust them to not betray your company you may end up doing more harm than good. To this end the best security for this would be to introduce controls which make it very difficult for insider threats to take place and be successful. This could be in the form of introducing high levels of controls on admin accounts, monitoring of activity and implementing zero trust architecture to make sure there are as few accounts with the possibility of being used by an insider as possible.
Also making sure that processes are stuck to for leavers or accounts which are no longer needed is paramount to your infrastructure's security, not leaving anything to chance.
The social engineering side of things is best handled by communicating with your employees and making sure they are sufficiently trained in dealing with phishing and other such social engineering attacks. This would usually look like introducing training so they can spot and deal with these attacks as they come, and routinely carrying out tests on employees to ensure they are vigilant.
Where Somerford can help
As the aforementioned security issues largely relate to data security, somerford are in a unique position to offer a wide range of partners which could aid in, or completely facilitate the security of your public cloud. From our knowledge and preventative security based partners such as Lacework FortiCNAPP, to our more active security based partners such as Netskope and Varonis, our security partners are able to offer a suite of services to aid you in protecting your public clouds.
Lacework FortiCNAPP
Lacework FortiCNAPP is a visibility focused cloud security solution which aims to give you a vast amount of insight into your data in your cloud estate. It works with cloud data from AWS, GCP and Azure providing a complete overview of the security of your data as well as any potential security risks relating to your cloud infrastructure. Whilst there are no active components of Lacework FortiCNAPP, meaning that all security fixes would have to be done manually, with assistance and guidance from Lacework FortiCNAPP, the insight provided by Lacework FortiCNAPP is invaluable to securing your public clouds. This would be the ideal solution if you wanted to know where you have weak security and there was potential for data being lost or exfiltrated.
Netskope
Netskope acts as a Cloud Security stack for your public cloud, offering protection through visibility, control and security to your organisation. Netskope allows for all your data to be monitored in near real time, and any suspicious activity to be alerted on and acted on. Alongside this, due to the inline nature of Netskope, insider threats can be all but eliminated allowing the most granular control on both your data to external parties and also users within your organisation. Netskope serves as a more active tool allowing you to create policies on your data and users which in turn allow for you to have your security as air tight as you see fit.
Okta & KnowBe4
These two solutions focus on the insider threat section that we previously discussed. Okta is all about identity management and access, allowing you to implement zero trust users as well as gain complete control and oversight of who is using your cloud and where they are using it, this would be a key tool in stopping the threat of a malicious insider user granting access to another entity or stealing data due to the level of controls you can put on both users and individual apps and data.
Knowbe4 on the other hand would be the perfect solution to ensuring that your workers and also customers are able to spot and handle potential social engineering attacks, most commonly in the form of phishing emails. Knowbe4 has a plethora of training relating to all facets of social engineering security which can be assigned to users as you see fit. As well as tools to deal with identified phishing emails such as the option for users to report emails as potential phishing to admins.
Conclusion
Somerford's partners are not limited to those above however, there are many more partners of ours which could facilitate your public cloud security. A key technology other than those listed for the aforementioned SOC would be something like Splunk ES.
Public clouds, whilst a powerful tool, have their own inherent security risks which must be considered when looking at the security of your data and infrastructure. Whilst the third party provider will cover some of it, there are still key aspects which need to be covered. We have discussed why this is the case, as well as the key threats to public clouds, alongside the best ways to remediate them, be that through training, policies or traditional security measures. We also looked at how Somerford's partners could potentially best align themselves to your security and where different vendors would fit into the jigsaw that is your security.
If you’d like to learn more about cloud infrastructure and security, or are interested in any of our partners and services for your cloud security needs and concerns, please get in touch or look through more of our cloud security material.







